Feature #7799
automated vulnerability scanning
90%
Related issues
History
#1 Updated by Greg Shah 10 months ago
We plan to update all of our dependencies to the latest stable levels as part of work on #6692 (Java 17). That will clear a large number of security problems. But it doesn't solve the longer term issue that we need a proces sto keep these up to date.
I want to implement the best practice of routinely scanning for vulnerabilities and moving to new versions of code that avoid those vulnerabilities. There are commercial services that can help with this, but they are expensive.
There are also vulnerability reports available in Maven which we can probably use to implement our own checks.
For example, from https://mvnrepository.com/ you can search on "snakeyaml" and find this page:
https://mvnrepository.com/artifact/org.yaml/snakeyaml
If you scroll way down to the really old version we use (1.15) you will see this:
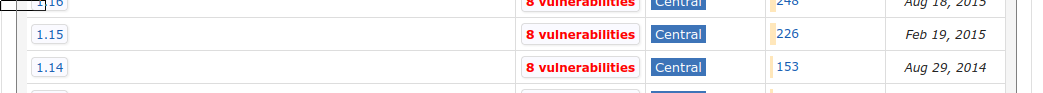
The data is public. If there is an open source tool to check this, I'd like to investigate using it. If not, perhaps we can build our own using the maven API and our list of dependencies.
#2 Updated by Greg Shah 10 months ago
- Related to Feature #6692: move FWD to Java 17 added
#3 Updated by Tomasz Domin 4 months ago
- File dependency-check-report.csv
 added
added - Status changed from New to WIP
- Assignee set to Tomasz Domin
I've implemented vulnerability checks in #6692 with org.owasp.dependencycheck plugin.
A sample report for FWD 6692a/14987 has been attached attached. By default only fwdAllRuntime configuration is checked.
It does not look bad, still waiting for JS libraries updates.
One or more dependencies were identified with known vulnerabilities in p2j_6692a: bootstrap-3.3.7-dist.zip: bootstrap.js (pkg:javascript/bootstrap@3.3.7) : CVE-2016-10735, CVE-2018-14041, CVE-2018-14042, CVE-2018-20676, CVE-2018-20677, CVE-2019-8331, Bootstrap before 4.0.0 is end-of-life and no longer maintained. bootstrap-3.3.7-dist.zip: bootstrap.min.js (pkg:javascript/bootstrap@3.3.7) : CVE-2016-10735, CVE-2018-14041, CVE-2018-14042, CVE-2018-20676, CVE-2018-20677, CVE-2019-8331, Bootstrap before 4.0.0 is end-of-life and no longer maintained. codegen-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 codegen-ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen-ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 common-2.2.3.jar (pkg:maven/org.eclipse.emf/common@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 commons-httpclient-3.1.jar (pkg:maven/commons-httpclient/commons-httpclient@3.1, cpe:2.3:a:apache:commons-httpclient:3.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:httpclient:3.1:*:*:*:*:*:*:*) : CVE-2012-5783, CVE-2020-13956 dom4j-1.6.1.jar (pkg:maven/dom4j/dom4j@1.6.1, cpe:2.3:a:dom4j_project:dom4j:1.6.1:*:*:*:*:*:*:*) : CVE-2020-10683, CVE-2018-1000632 ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-change-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-change@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-xmi-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-xmi@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 fwd-h2-1.40-trunk.jar (pkg:maven/com.goldencode/fwd-h2@1.40-trunk, cpe:2.3:a:h2database:h2:1.40:*:*:*:*:*:*:*) : CVE-2021-42392, CVE-2022-23221, CVE-2021-23463, CVE-2022-45868 fwd-imageio-bmp-3.1.2.jar (pkg:maven/com.twelvemonkeys.imageio/fwd-imageio-bmp@3.1.2, cpe:2.3:a:twelvemonkeys_project:twelvemonkeys:3.1.2:*:*:*:*:*:*:*) : CVE-2021-23792 gremlin-shaded-3.7.0.jar/META-INF/maven/com.fasterxml.jackson.core/jackson-databind/pom.xml (pkg:maven/com.fasterxml.jackson.core/jackson-databind@2.15.2, cpe:2.3:a:fasterxml:jackson-databind:2.15.2:*:*:*:*:*:*:*, cpe:2.3:a:fasterxml:jackson-modules-java8:2.15.2:*:*:*:*:*:*:*) : CVE-2023-35116 gwtbootstrap3-1.0.1.jar: bootstrap-3.4.1.min.cache.js (pkg:javascript/bootstrap@3.4.1.min.cache) : Bootstrap before 4.0.0 is end-of-life and no longer maintained. gwtbootstrap3-1.0.1.jar: jquery-1.12.4.min.cache.js (pkg:javascript/jquery@1.12.4.min.cache) : CVE-2015-9251, CVE-2019-11358, CVE-2020-11022, CVE-2020-11023, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates gwtbootstrap3-extras-1.0.2.jar: bootstrap-select-1.12.4.min.cache.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: jquery-ui-1.11.2.custom.min.cache.js (pkg:javascript/jquery-ui@1.11.2) : CVE-2021-41182, CVE-2021-41183, CVE-2021-41184, CVE-2022-31160 gwtbootstrap3-extras-1.0.2.jar: moment-2.9.0.min.cache.js (pkg:javascript/moment.js@2.9.0.min.cache) : CVE-2017-18214, CVE-2022-24785, CVE-2016-4055, Regular Expression Denial of Service (ReDoS) gwtbootstrap3-extras-1.0.2.jar: typeahead.jquery-0.10.5.min.cache.js (pkg:javascript/jquery@0.10.5.min.cache) : CVE-2012-6708, CVE-2020-7656, CVE-2011-4969, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates itext-2.1.7.jar (pkg:maven/com.lowagie/itext@2.1.7) : CVE-2017-9096 itextpdf-5.5.13.3.jar (pkg:maven/com.itextpdf/itextpdf@5.5.13.3, cpe:2.3:a:itextpdf:itext:5.5.13.3:*:*:*:*:*:*:*) : CVE-2022-24196, CVE-2022-24197 ivy-2.5.1.jar (pkg:maven/org.apache.ivy/ivy@2.5.1, cpe:2.3:a:apache:ant:2.5.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:ivy:2.5.1:*:*:*:*:*:*:*) : CVE-2022-46751 jquery-3.2.1.zip: jquery-3.2.1.js (pkg:javascript/jquery@3.2.1) : CVE-2019-11358, CVE-2020-11022, CVE-2020-11023 jquery-ui-1.12.1.custom.zip: jquery-ui.js (pkg:javascript/jquery-ui@1.12.1) : CVE-2021-41182, CVE-2021-41183, CVE-2021-41184, CVE-2022-31160 jquery-ui-1.12.1.custom.zip: jquery-ui.min.js (pkg:javascript/jquery-ui@1.12.1) : CVE-2021-41182, CVE-2021-41183, CVE-2021-41184, CVE-2022-31160 jquery-ui-1.12.1.custom.zip: jquery.js (pkg:javascript/jquery@1.12.4) : CVE-2015-9251, CVE-2019-11358, CVE-2020-11022, CVE-2020-11023, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates log4j-1.2.17.jar (pkg:maven/log4j/log4j@1.2.17, cpe:2.3:a:apache:log4j:1.2.17:*:*:*:*:*:*:*) : CVE-2019-17571, CVE-2020-9493, CVE-2022-23305, CVE-2022-23302, CVE-2022-23307, CVE-2021-4104, CVE-2023-26464 quartz-2.3.2.jar (pkg:maven/org.quartz-scheduler/quartz@2.3.2, cpe:2.3:a:softwareag:quartz:2.3.2:*:*:*:*:*:*:*) : CVE-2023-39017 velocity-1.7.jar (pkg:maven/org.apache.velocity/velocity@1.7, cpe:2.3:a:apache:velocity_engine:1.7:*:*:*:*:*:*:*) : CVE-2020-13936 xercesImpl-2.12.2.jar (pkg:maven/xerces/xercesImpl@2.12.2, cpe:2.3:a:apache:xerces-j:2.12.2:*:*:*:*:*:*:*) : CVE-2017-10355 xsd-2.2.3.jar (pkg:maven/org.eclipse.xsd/xsd@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218
#4 Updated by Tomasz Domin 3 months ago
A report for FWD 6692a/15172, there should be less vulnerabilities, but in meantime a new ones has been discovered so components need upgraded again.
apache-mime4j-core-0.8.9.jar (pkg:maven/org.apache.james/apache-mime4j-core@0.8.9) : CVE-2024-21742 bcprov-jdk18on-1.77.jar (pkg:maven/org.bouncycastle/bcprov-jdk18on@1.77, cpe:2.3:a:bouncycastle:bouncy-castle-crypto-package:1.77:*:*:*:*:*:*:*, cpe:2.3:a:bouncycastle:bouncy_castle_crypto_package:1.77:*:*:*:*:*:*:*, cpe:2.3:a:bouncycastle:bouncy_castle_for_java:1.77:*:*:*:*:*:*:*, cpe:2.3:a:bouncycastle:legion-of-the-bouncy-castle:1.77:*:*:*:*:*:*:*, cpe:2.3:a:bouncycastle:legion-of-the-bouncy-castle-java-crytography-api:1.77:*:*:*:*:*:*:*, cpe:2.3:a:bouncycastle:the_bouncy_castle_crypto_package_for_java:1.77:*:*:*:*:*:*:*) : CVE-2024-29857, CVE-2024-30171, CVE-2024-30172 bootstrap-3.4.1.jar (pkg:javascript/bootstrap@3.4.1, pkg:maven/org.webjars/bootstrap@3.4.1) : Bootstrap before 4.0.0 is end-of-life and no longer maintained. codegen-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 codegen-ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen-ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 common-2.2.3.jar (pkg:maven/org.eclipse.emf/common@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 commons-configuration-1.10.jar (pkg:maven/commons-configuration/commons-configuration@1.10, cpe:2.3:a:apache:commons_configuration:1.10:*:*:*:*:*:*:*) : CVE-2024-29131, CVE-2024-29133 commons-configuration2-2.9.0.jar (pkg:maven/org.apache.commons/commons-configuration2@2.9.0, cpe:2.3:a:apache:commons_configuration:2.9.0:*:*:*:*:*:*:*) : CVE-2024-29131, CVE-2024-29133 commons-httpclient-3.1.jar (pkg:maven/commons-httpclient/commons-httpclient@3.1, cpe:2.3:a:apache:commons-httpclient:3.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:httpclient:3.1:*:*:*:*:*:*:*) : CVE-2012-5783, CVE-2020-13956 ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-change-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-change@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-xmi-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-xmi@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 fwd-h2-1.45-trunk.jar (pkg:maven/com.goldencode/fwd-h2@1.45-trunk, cpe:2.3:a:h2database:h2:1.45:*:*:*:*:*:*:*) : CVE-2021-42392, CVE-2022-23221, CVE-2021-23463, CVE-2022-45868 gremlin-shaded-3.7.0.jar/META-INF/maven/com.fasterxml.jackson.core/jackson-databind/pom.xml (pkg:maven/com.fasterxml.jackson.core/jackson-databind@2.15.2, cpe:2.3:a:fasterxml:jackson-databind:2.15.2:*:*:*:*:*:*:*, cpe:2.3:a:fasterxml:jackson-modules-java8:2.15.2:*:*:*:*:*:*:*) : CVE-2023-35116 gwtbootstrap3-1.0.1.jar: bootstrap-3.4.1.min.cache.js (pkg:javascript/bootstrap@3.4.1.min.cache) : Bootstrap before 4.0.0 is end-of-life and no longer maintained. gwtbootstrap3-1.0.1.jar: jquery-1.12.4.min.cache.js (pkg:javascript/jquery@1.12.4.min.cache) : CVE-2015-9251, CVE-2019-11358, CVE-2020-11022, CVE-2020-11023, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates gwtbootstrap3-extras-1.0.2.jar: bootstrap-select-1.12.4.min.cache.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: jquery-ui-1.11.2.custom.min.cache.js (pkg:javascript/jquery-ui@1.11.2) : CVE-2021-41182, CVE-2021-41183, CVE-2021-41184, CVE-2022-31160 gwtbootstrap3-extras-1.0.2.jar: moment-2.9.0.min.cache.js (pkg:javascript/moment.js@2.9.0.min.cache) : CVE-2017-18214, CVE-2022-24785, CVE-2016-4055, Regular Expression Denial of Service (ReDoS) gwtbootstrap3-extras-1.0.2.jar: typeahead.jquery-0.10.5.min.cache.js (pkg:javascript/jquery@0.10.5.min.cache) : CVE-2012-6708, CVE-2020-7656, CVE-2011-4969, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates itextpdf-5.5.6.jar (pkg:maven/com.itextpdf/itextpdf@5.5.6, cpe:2.3:a:itextpdf:itext:5.5.6:*:*:*:*:*:*:*) : CVE-2017-9096, CVE-2022-24196, CVE-2022-24197 ivy-2.5.1.jar (pkg:maven/org.apache.ivy/ivy@2.5.1, cpe:2.3:a:apache:ant:2.5.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:ivy:2.5.1:*:*:*:*:*:*:*) : CVE-2022-46751 jfreechart-1.0.19.jar (pkg:maven/org.jfree/jfreechart@1.0.19, cpe:2.3:a:time_project:time:1.0.19:*:*:*:*:*:*:*) : CVE-2023-52070, CVE-2024-22949, CVE-2024-23076 postgresql-42.7.1.jar (pkg:maven/org.postgresql/postgresql@42.7.1, cpe:2.3:a:postgresql:postgresql_jdbc_driver:42.7.1:*:*:*:*:*:*:*) : CVE-2024-1597 quartz-2.3.2.jar (pkg:maven/org.quartz-scheduler/quartz@2.3.2, cpe:2.3:a:softwareag:quartz:2.3.2:*:*:*:*:*:*:*) : CVE-2023-39017 velocity-1.7.jar (pkg:maven/org.apache.velocity/velocity@1.7, cpe:2.3:a:apache:velocity_engine:1.7:*:*:*:*:*:*:*) : CVE-2020-13936 xercesImpl-2.12.2.jar (pkg:maven/xerces/xercesImpl@2.12.2, cpe:2.3:a:apache:xerces-j:2.12.2:*:*:*:*:*:*:*) : CVE-2017-10355 xsd-2.2.3.jar (pkg:maven/org.eclipse.xsd/xsd@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218
#5 Updated by Tomasz Domin 30 days ago
- Status changed from WIP to Review
The feature has been merged into trunk with #6692
In order to check
./gradlew dependencyCheckAnalyze
HTML- build/reports/dependency-check-report.htmlCSV- build/reports/dependency-check-report.html
Please review.
#6 Updated by Greg Shah 28 days ago
I just ran it, here is the output:
To honour the JVM settings for this build a single-use Daemon process will be forked. See https://docs.gradle.org/7.6.4/userguide/gradle_daemon.html#sec:disabling_the_daemon. Daemon will be stopped at the end of the build > Configure project : [ant:echo] propArg: > Task :dependencyCheckAnalyze Verifying dependencies for project trunk Checking for updates and analyzing dependencies for vulnerabilities An NVD API Key was not provided - it is highly recommended to use an NVD API key as the update can take a VERY long time without an API Key ---------------------------------------------------- .NET Assembly Analyzer could not be initialized and at least one 'exe' or 'dll' was scanned. The 'dotnet' executable could not be found on the path; either disable the Assembly Analyzer or add the path to dotnet core in the configuration. The dotnet 6.0 core runtime or SDK is required to analyze assemblies ---------------------------------------------------- No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/388/jquery-loading-overlay-1.5.3/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/397/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/35/META-INF/resources/webjars/d3/4.13.0/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/391/tabulator-master-2.12.0/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/386/cbtree-v0.9.4-0/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/396/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/395/gettext.js-1.2.0/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/395/gettext.js-1.2.0/package-lock.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/385/adamwdraper-Numeral-js-7de892f/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/384/dojo-1.17.3/dojox/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/398/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/399/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/390/material-design-icons/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/37/META-INF/resources/webjars/jquery-ui/1.13.2/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/384/dojo-1.17.3/dojo/package-lock.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/384/dojo-1.17.3/dojo/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check No lock file exists - this will result in false negatives; please run `npm install --package-lock` Analyzing `/tmp/dctempbe183bb4-cca6-47d6-b55b-3f41451a9c3a/check7332221016722343505tmp/384/dojo-1.17.3/dijit/package.json` - however, the node_modules directory does not exist. Please run `npm install` prior to running dependency-check > Task :dependencyCheckAnalyze Generating report for project trunk Found 119 vulnerabilities in project trunk One or more dependencies were identified with known vulnerabilities in trunk: bootstrap-3.4.1.jar (pkg:javascript/bootstrap@3.4.1, pkg:maven/org.webjars/bootstrap@3.4.1) : Bootstrap before 4.0.0 is end-of-life and no longer maintained. codegen-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 codegen-ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/codegen-ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 common-2.2.3.jar (pkg:maven/org.eclipse.emf/common@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 commons-configuration-1.10.jar (pkg:maven/commons-configuration/commons-configuration@1.10, cpe:2.3:a:apache:commons_configuration:1.10:*:*:*:*:*:*:*) : CVE-2024-29131, CVE-2024-29133 commons-configuration2-2.9.0.jar (pkg:maven/org.apache.commons/commons-configuration2@2.9.0, cpe:2.3:a:apache:commons_configuration:2.9.0:*:*:*:*:*:*:*) : CVE-2024-29131, CVE-2024-29133 commons-httpclient-3.1.jar (pkg:maven/commons-httpclient/commons-httpclient@3.1, cpe:2.3:a:apache:commons-httpclient:3.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:httpclient:3.1:*:*:*:*:*:*:*) : CVE-2012-5783, CVE-2020-13956 ecore-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-change-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-change@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 ecore-xmi-2.2.3.jar (pkg:maven/org.eclipse.emf/ecore-xmi@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 fwd-h2-1.48-trunk.jar (pkg:maven/com.goldencode/fwd-h2@1.48-trunk, cpe:2.3:a:h2database:h2:1.48:*:*:*:*:*:*:*) : CVE-2021-42392, CVE-2022-23221, CVE-2021-23463, CVE-2022-45868 gremlin-shaded-3.7.0.jar/META-INF/maven/com.fasterxml.jackson.core/jackson-databind/pom.xml (pkg:maven/com.fasterxml.jackson.core/jackson-databind@2.15.2, cpe:2.3:a:fasterxml:jackson-databind:2.15.2:*:*:*:*:*:*:*, cpe:2.3:a:fasterxml:jackson-modules-java8:2.15.2:*:*:*:*:*:*:*) : CVE-2023-35116 gwtbootstrap3-1.0.1.jar: bootstrap-3.4.1.min.cache.js (pkg:javascript/bootstrap@3.4.1.min.cache) : Bootstrap before 4.0.0 is end-of-life and no longer maintained. gwtbootstrap3-1.0.1.jar: jquery-1.12.4.min.cache.js (pkg:javascript/jquery@1.12.4.min.cache) : CVE-2015-9251, CVE-2019-11358, CVE-2020-11022, CVE-2020-11023, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates gwtbootstrap3-extras-1.0.2.jar: bootstrap-select-1.12.4.min.cache.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ar_AR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-bg_BG.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cro_CRO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-cs_CZ.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-da_DK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-de_DE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-en_US.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-es_CL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-et_EE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-eu.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fa_IR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fi_FI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-fr_FR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-hu_HU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-id_ID.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-it_IT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ja_JP.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-kh_KM.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ko_KR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-lt_LT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nb_NO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-nl_NL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pl_PL.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_BR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-pt_PT.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ro_RO.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ru_RU.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sk_SK.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sl_SI.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-sv_SE.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-tr_TR.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-ua_UA.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-vi_VN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_CN.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: defaults-zh_TW.min.js (pkg:javascript/bootstrap-select@1.12.4) : CVE-2019-20921 gwtbootstrap3-extras-1.0.2.jar: jquery-ui-1.11.2.custom.min.cache.js (pkg:javascript/jquery-ui@1.11.2) : CVE-2021-41182, CVE-2021-41183, CVE-2021-41184, CVE-2022-31160 gwtbootstrap3-extras-1.0.2.jar: moment-2.9.0.min.cache.js (pkg:javascript/moment.js@2.9.0.min.cache) : CVE-2017-18214, CVE-2022-24785, CVE-2016-4055, Regular Expression Denial of Service (ReDoS) gwtbootstrap3-extras-1.0.2.jar: typeahead.jquery-0.10.5.min.cache.js (pkg:javascript/jquery@0.10.5.min.cache) : CVE-2012-6708, CVE-2020-7656, CVE-2011-4969, jQuery 1.x and 2.x are End-of-Life and no longer receiving security updates itextpdf-5.5.6.jar (pkg:maven/com.itextpdf/itextpdf@5.5.6, cpe:2.3:a:itextpdf:itext:5.5.6:*:*:*:*:*:*:*) : CVE-2017-9096, CVE-2022-24196, CVE-2022-24197 ivy-2.5.1.jar (pkg:maven/org.apache.ivy/ivy@2.5.1, cpe:2.3:a:apache:ant:2.5.1:*:*:*:*:*:*:*, cpe:2.3:a:apache:ivy:2.5.1:*:*:*:*:*:*:*) : CVE-2022-46751 jetty-servlets-9.4.54.v20240208.jar (pkg:maven/org.eclipse.jetty/jetty-servlets@9.4.54.v20240208, cpe:2.3:a:eclipse:jetty:9.4.54:20240208:*:*:*:*:*:*, cpe:2.3:a:jetty:jetty:9.4.54:20240208:*:*:*:*:*:*, cpe:2.3:a:mortbay_jetty:jetty:9.4.54:20240208:*:*:*:*:*:*) : CVE-2023-36479 jfreechart-1.0.19.jar (pkg:maven/org.jfree/jfreechart@1.0.19, cpe:2.3:a:time_project:time:1.0.19:*:*:*:*:*:*:*) : CVE-2023-52070, CVE-2024-22949, CVE-2024-23076 quartz-2.3.2.jar (pkg:maven/org.quartz-scheduler/quartz@2.3.2, cpe:2.3:a:softwareag:quartz:2.3.2:*:*:*:*:*:*:*) : CVE-2023-39017 velocity-1.7.jar (pkg:maven/org.apache.velocity/velocity@1.7, cpe:2.3:a:apache:velocity_engine:1.7:*:*:*:*:*:*:*) : CVE-2020-13936 xercesImpl-2.12.2.jar (pkg:maven/xerces/xercesImpl@2.12.2, cpe:2.3:a:apache:xerces-j:2.12.2:*:*:*:*:*:*:*) : CVE-2017-10355 xsd-2.2.3.jar (pkg:maven/org.eclipse.xsd/xsd@2.2.3, cpe:2.3:a:eclipse:org.eclipse.core.runtime:2.2.3:*:*:*:*:*:*:*) : CVE-2023-4218 See the dependency-check report for more details. Region [NODEAUDIT] : Not alive and dispose was called, filename: NODEAUDIT Region [CENTRAL] : Not alive and dispose was called, filename: CENTRAL Region [POM] : Not alive and dispose was called, filename: POM Deprecated Gradle features were used in this build, making it incompatible with Gradle 8.0. You can use '--warning-mode all' to show the individual deprecation warnings and determine if they come from your own scripts or plugins. See https://docs.gradle.org/7.6.4/userguide/command_line_interface.html#sec:command_line_warnings BUILD SUCCESSFUL in 22m 1s 1 actionable task: 1 executed
#7 Updated by Greg Shah 28 days ago
If you run cat <scan_output> | grep -o "CVE-[0-9]*-[0-9]*" | sort | uniq, you get:
CVE-2011-4969 CVE-2012-5783 CVE-2012-6708 CVE-2015-9251 CVE-2016-4055 CVE-2017-10355 CVE-2017-18214 CVE-2017-9096 CVE-2019-11358 CVE-2019-20921 CVE-2020-11022 CVE-2020-11023 CVE-2020-13936 CVE-2020-13956 CVE-2020-7656 CVE-2021-23463 CVE-2021-41182 CVE-2021-41183 CVE-2021-41184 CVE-2021-42392 CVE-2022-23221 CVE-2022-24196 CVE-2022-24197 CVE-2022-24785 CVE-2022-31160 CVE-2022-45868 CVE-2022-46751 CVE-2023-35116 CVE-2023-36479 CVE-2023-39017 CVE-2023-4218 CVE-2023-52070 CVE-2024-22949 CVE-2024-23076 CVE-2024-29131 CVE-2024-29133
#8 Updated by Greg Shah 28 days ago
You can lookup details of a CVE-2011-4969 using https://nvd.nist.gov/vuln/detail/cve-2011-4969
#9 Updated by Greg Shah 28 days ago
NIST (National Institute for Standards and Technology) is an agency of the US government. It creates standards, runs services like an atomic clock. Amoung many other things, it maintains the NVD (National Vulnerability Database) which tracks CVEs (Common Vulnerabilities and Exposures).
The NVD provides an API. We should consider a tool (maybe writing one ourselves if needed) that uses the output from the security scan to write a report that actually provides details on each vulnerability.
#10 Updated by Greg Shah 28 days ago
- Status changed from Review to WIP
- % Done changed from 0 to 70
This is a good start but we will need to refine the results as noted in #7799-9. We must make it very easy to evaluate the output of the scan. If we have to manually pull all the details ourselves, it would greatly slow us down.
#11 Updated by Tomasz Domin 27 days ago
Greg Shah wrote:
This is a good start but we will need to refine the results as noted in #7799-9. We must make it very easy to evaluate the output of the scan. If we have to manually pull all the details ourselves, it would greatly slow us down.
Greg, have you tried to browse generated HTML report build/reports/dependency-check-report.html ?
I think its all there.
e.g.
gremlin-shaded-3.7.0.jar (shaded: com.fasterxml.jackson.core:jackson-databind:2.15.2)
Description:
General data-binding functionality for Jackson: works on core streaming API
License:
The Apache Software License, Version 2.0: https://www.apache.org/licenses/LICENSE-2.0.txt
File Path: /home/tjd/.gradle/caches/modules-2/files-2.1/org.apache.tinkerpop/gremlin-shaded/3.7.0/bd140102a3a474b54a35c24bc400be58cd42bc63/gremlin-shaded-3.7.0.jar/META-INF/maven/com.fasterxml.jackson.core/jackson-databind/pom.xml
MD5: 07fbb2e4e4728d273e8680e1a08b6b02
SHA1: aa7009c05985af917eed65e44e7b9c1020c8bf6f
SHA256:9863596d8c05d5e29de83ac84586b24c896f9ba06544b8f23c6dde64e7ed6e9c
Referenced In Project/Scope: p2j_6692a:fwdAllRuntime
Evidence
Identifiers
pkg:maven/com.fasterxml.jackson.core/jackson-databind@2.15.2 (Confidence:High)
cpe:2.3:a:fasterxml:jackson-databind:2.15.2:*:*:*:*:*:*:* (Confidence:Highest)
cpe:2.3:a:fasterxml:jackson-modules-java8:2.15.2:*:*:*:*:*:*:* (Confidence:Low)
Published Vulnerabilities
CVE-2023-35116
jackson-databind through 2.15.2 allows attackers to cause a denial of service or other unspecified impact via a crafted object that uses cyclic dependencies. NOTE: the vendor's perspective is that this is not a valid vulnerability report, because the steps of constructing a cyclic data structure and trying to serialize it cannot be achieved by an external attacker.
CWE-770 Allocation of Resources Without Limits or Throttling
CVSSv3:
Base Score: MEDIUM (4.7)
Vector: CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H/E:1.0/RC:R/MAV:A
References:
cve@mitre.org - ISSUE_TRACKING
Vulnerable Software & Versions:
cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:* versions up to (excluding) 2.16.0